hacked Archive

Obama wants a programme to sanction hackers
A new program that allows the government to punish foreign hackers was urged by US President to be created. The government will now be able to target those attempting cyber attacks on US assets and infrastructure and sanction hackers. “Cyber-threats are one of the most serious economic and national security

How to know if you have been hacked
81% of large businesses have suffered malicious data breaches shows in a cybersecurity survey, made by UK Government’s in 2014. That indicate almost one in five didn’t. “In this context, it’s impractical to prove a negative,” said Lenny Zeltser, a senior faculty member at the SANS Institute, who
Gamers targeted by CryptoLocker, a ransomware virus
I was telling some time ago about a type of virus, ransomware which basically encrypts your data and you can not regain access unless you pay an amount of money as a reward. CryptoLocker has a new variant which targets gamers and stop them playing their favourite games unless they pay a

Dozens arrested in cybercrime raids
The UK’s National Crime Agency has arrested this week 56 suspected hackers as part of a “strike week” against cybercrime. In total, 25 separate operations were carried out across The United Kingdom. Those arrested are suspected of being involved in a wide variety of cybercrimes including data theft,

Superfish: Lenovo is only the tip of the iceberg
In Malware
Security experts from G Data SecurityLabs analyzed Superfish adware. In this process, analysts have encountered in program, a technology component, called SSL digestion. It uses a root certificate which is poorly secured and has extensive rights on the computer. SSL Digestor intercept safe HTTPS connections which can be decrypted.

Federal Communications Commission approve net neutrality rules
The Federal Communications Commission on Thursday voted to approve new rules on how the internet should be governed. New rules will prohibit internet service providers from discriminating against content producers. “Who determines how you use the internet? Who decides what content you can view and when? Should there

Android phones can be tracked just with battery power alone
We all know that a phone uses more power the further away it is from a cell tower as it tries to connect. So, an Android phone can be tracked by studying their power use over time, without using their GPS or wi-fi/data usage. Extra power is used by

PwC: cyber attacks caused damage to companies estimated at 2.7 billion. dollars
Number of cyber security incidents detected in companies in 2014 increased by 48% over the previous year, reaching 42.8 million global events, apparent from an analysis performed by PwC – The Global State of Information Security Survey 2015, based on the responses of 9,700 managers responsible
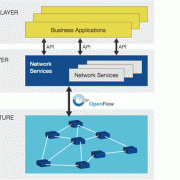
Software Defined Networking (SDN), the next Eldorado of IT
Few people know , SDN has everything it takes to become a new standard of IT. Basically, SDN brings a global expansion of virtualization from hardware and storage to further infrastructure networks. Thus, interventions on the networks will not require a manual configuration, a direct intervention
Forbes.com attacked by Chinese hackers
Chinese hackers attacked Forbes.com web site with an malicious software (malware) that target only certain visitors, which include several US defense institutions and financial services, according to cyber security companies, iSIGHT. According to iSIGHT and Invincea, someone compromised this application for three days (November 28 until December 1, 2014) or
