Malware Archive
Edward Snowden on FBI vs Apple
In Malware
In a recent Tweet, Edward Snowden says that there are some crucial details in the FBI vs Apple case being obscured by the officials. Below you can find a list with Snowden’s conclusions: 1. The FBI already has all of the suspect’s communications records — who they

From now on, you can watch videos on YouTube without advertising!
In Malware
Online video platform YouTube, a subsidiary of Google, announced Wednesday the launch of a subscription that allows users to watch videos without advertising, writes AFP. The offer will be launched in the US on October 28, priced at 9.99 dollars a month, the group said. YouTube said

Siri interrupted a press conference at the White House(video)
In Malware
Virtual Personal Assistant Siri, available on some Apple products, including mobile phones, has interrupted a session press inquiries held at the White House, answering to a journalist before he got to finish what he had to say, writes The Guardian. American journalist had asked the press
Stagefright Detector, a must have Android mobile application
In Malware
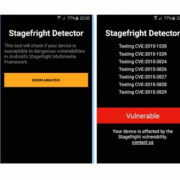
Stagefright is the worst nightmare that an Android owner can have. This is the android vulnerability discovered by Joshua J. Drake, from the Zimperium Mobile Security. I described this android vulnerability in an earlier post, called Critical Android phones Vulnerability. Stagefright spreads via MMS and once it
The FANTASTIC 5G project for 5G networks
In Malware
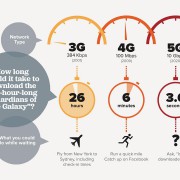
FANTASTIC 5G project is developing a new radio interface below 6 GHz for 5G networks. A group of 16 leading telecoms players are joining forces to speed up the development of a new 6 GHz radio interfaces for 5G networks. The “FANTASTIC 5G” (Flexible Air Interface for Scalable Service Delivery

Superfish: Lenovo is only the tip of the iceberg
In Malware
Security experts from G Data SecurityLabs analyzed Superfish adware. In this process, analysts have encountered in program, a technology component, called SSL digestion. It uses a root certificate which is poorly secured and has extensive rights on the computer. SSL Digestor intercept safe HTTPS connections which can be decrypted.

A faster and better standardized Web: Google renounce to SPDY in favor of HTTP / 2
In Malware, Technology
The SPDY protocol was announced by Google in November 2009 and implemented for the first time a year later. SPDY protocol aimed to optimize the old HTTP by implementing compression technologies, multiplexing and encryption. Although it is currently implemented in most browsers, the protocol has not received wide
The Carbanak hacking group stole $1 billion from the accounts of several banks
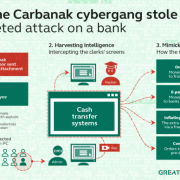
A group of hackers called Carbanak stole about $1 billion from the accounts of several banks and financial sector companies around the world from 2013 to the present, in a unprecedented banking hack, said the cyber security company from Russia, Kaspersky Lab. The group, called “Carbanak” by

Cloud, a new era of innovation for personal data protection
In Malware
A sophisticated cryptographic algorithm prevents unwanted distribution of personal data, including credit card details. IBM researchers have recently announced their intention to develop a technology based on cloud platform that will help users, giving a better protection for their personal data, when they are online, including date of birth,

Tricked by email. Ukrainian government officials have been spied on by hackers which have been used a Windows vulnerability
Hackers have used this summer an error of the Microsoft Windows operating system to spy Ukrainian officials and American academics. This is the conclusion of an investigation of an American company in the field of cybersecurity, reports the Wall Street Journal (WSJ). According to the publication,
- 1
- 2
