hacker news Archive
Hacker News was hacked? Characters Vulnerability found
Today I discovered an interesting vulnerability in the Ycombinator’s Hacker News website. For those of you who don’t know what’s all about this website, below I added a short description of it: Hacker News is a social news website focusing on computer science and entrepreneurship. It is

Github under DDOS attack
In Cyber Attack
Github is under massive DDOS attack coming from China. This attack started on 26 March 2015, and the main attacker is Baidu. On it’s service status page, Github posted on 26 March this message: We’ve identified and mitigated a DoS attack that was impacting service. Service is

Tracking the FREAK ATACK, a huge SSL security flaw
Called Freak, Factoring attack on RSA-EXPORT Keys, the security breach exists on high-profile websites. It is supossed that seven hours is all it takes to crack the encryption that is in place on some supposedly secure websites. Browsers can be hijacked and tricked into accessing websites using legacy encryption. There was

Uber database breach exposed 50000 drivers
Uber released a statement on Friday announcing that it suffered a data breach in 2014 that affected 50 000 Uber drivers across the United States. The Uber’s database was accessed by an unauthorized third party. Uber says that 50 000 driver partner names and driver’s license numbers
HHVM vs PHP 5 battle. HHVM is much faster
In Programming
HHVM vs PHP is a battle that you should consider. Which one is more faster. Is HHVM more performant than PHP? Does HHVM consume less CPU than PHP? Which one is more stable and which one could be used in production? These are questions that might get

2014 Security News Review
In this article you’ll find the hottest hacking news from 2014. Below you’ll find the most important security news for each month of 2014. All titles are selected from our hacking news blog. We hope you enjoyed reading these news and we assure you that better quality
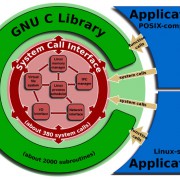
GHOST glibc vulnerability (CVE-2015-0235) affects Linux Machines
A critical vulnerability has been found in glibc, the GNU C library, that affects almost all Linux systems dating back to 2000. Attackers can use this flaw to execute code and remotely gain control of Linux machines. The Red Hat Product Security has been made aware of
