Top Cybersecurity Data Breaches of 2023
The year 2023 witnessed an alarming surge in cyber threats, leaving a trail of compromised data across various sectors globally. From healthcare giants to renowned tech companies, no industry seemed impervious to the escalating wave of cyber attacks. Here’s a recap of some of the most significant
Enhancing Cybersecurity: The Imperative of Biometric Authentication and the Intricacies of Typing Biometrics
In an era defined by rapid technological advancements, safeguarding sensitive information has become paramount. As cyber threats continue to evolve, traditional methods of authentication, such as passwords, are no longer sufficient to protect against sophisticated attacks. Biometric authentication has emerged as a must-have security measure, offering a

Top 10 Cyber Security incidents from the last years
There have been many significant cyber security incidents in recent years, and it is difficult to rank them in terms of their importance or impact. Here is a list of ten examples of significant cyber security incidents that have occurred in the past few years: The WannaCry

Microsoft adds VPN to its Edge browser and enables it by default
Microsoft added VPN to its Edge browser VPN stands for Virtual Private Network. A VPN creates a secure connection between two devices and encrypts data being transmitted over the Internet. This makes it difficult for hackers to intercept and steal information. With the addition of VPN to

Uber, the victim of a cyber attack. A hacker broke into the network
Uber is investigating a cyber attack, after a hacker allegedly sent security experts evidence of the attack on its network. A hacker sent several security experts images proving that he had access to the Uber network. They received images showing the structure of the cloud and part
Protectumus – Website Security & Performance, WAF, Antivirus and 2FA services provider
Protectumus is a Website Security & Performance provider that combines AI and Machine Learning to detect attacks, protect against malware and recover in case of being hacked. Everything you need to know about Protectumus and how it works We are surrounded by the advanced level of technology

The date for DefCamp Capture the Flag (D-CTF) is 11-13 February 2022
Are you ready to compete & win DefCamp Capture the Flag (D-CTF)? Hi ! We hope you managed to recharge during the winter holidays and you started the new year with full speed ahead ‘cause we sure did. As you are well aware, DefCamp Capture the Flag (D-CTF) has
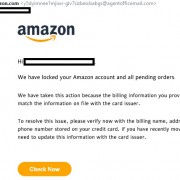
Be aware of Amazon phishing and scam attempts
In Cyber Crime
Before clicking any buttons and links from your email messages, you should first check the real sender and also the links behind buttons, images and other texts. In this article we will cover an example of scam phishing attemp that targets Amazon customers. Amazon.com, Inc. is an

Typing AI Biometrics revolutionizes online security by creating a secure typing biometrics authentication solution
Although passwords seem to be pretty secure, they can still be cracked, and hackers come up with newer techniques every other day. One thing that cannot be cracked is your biometrics but things like deep fake technology still crack that to some extent. In that case, your

Be aware of ICANN Phishing and Scam attempts
ICANN phishing attempts target domain owners and, in recent cases, hackers target first time domain registration companies and persons with sophisticated scam attempts. The Internet Corporation for Assigned Names and Numbers (ICANN) is an American multistakeholder group and nonprofit organization responsible for coordinating the maintenance and procedures