hacking Archive

Can driverless cars be hacked ?
Driverless cars could be vulnerable to hackers who could bring cities to a chaos, steal cars remotely or even commit deadly terror attacks, and many other problems, is a known fact. The report from the Institution of Engineering and Technology (IET) suggests that autonomous vehicles could be on the roads in

Tracking the FREAK ATACK, a huge SSL security flaw
Called Freak, Factoring attack on RSA-EXPORT Keys, the security breach exists on high-profile websites. It is supossed that seven hours is all it takes to crack the encryption that is in place on some supposedly secure websites. Browsers can be hijacked and tricked into accessing websites using legacy encryption. There was

Superfish: Lenovo is only the tip of the iceberg
In Malware
Security experts from G Data SecurityLabs analyzed Superfish adware. In this process, analysts have encountered in program, a technology component, called SSL digestion. It uses a root certificate which is poorly secured and has extensive rights on the computer. SSL Digestor intercept safe HTTPS connections which can be decrypted.

Uber database breach exposed 50000 drivers
Uber released a statement on Friday announcing that it suffered a data breach in 2014 that affected 50 000 Uber drivers across the United States. The Uber’s database was accessed by an unauthorized third party. Uber says that 50 000 driver partner names and driver’s license numbers

Federal Communications Commission approve net neutrality rules
The Federal Communications Commission on Thursday voted to approve new rules on how the internet should be governed. New rules will prohibit internet service providers from discriminating against content producers. “Who determines how you use the internet? Who decides what content you can view and when? Should there

Android phones can be tracked just with battery power alone
We all know that a phone uses more power the further away it is from a cell tower as it tries to connect. So, an Android phone can be tracked by studying their power use over time, without using their GPS or wi-fi/data usage. Extra power is used by

PwC: cyber attacks caused damage to companies estimated at 2.7 billion. dollars
Number of cyber security incidents detected in companies in 2014 increased by 48% over the previous year, reaching 42.8 million global events, apparent from an analysis performed by PwC – The Global State of Information Security Survey 2015, based on the responses of 9,700 managers responsible
Forbes.com attacked by Chinese hackers
Chinese hackers attacked Forbes.com web site with an malicious software (malware) that target only certain visitors, which include several US defense institutions and financial services, according to cyber security companies, iSIGHT. According to iSIGHT and Invincea, someone compromised this application for three days (November 28 until December 1, 2014) or
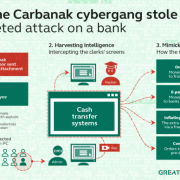
The Carbanak hacking group stole $1 billion from the accounts of several banks
A group of hackers called Carbanak stole about $1 billion from the accounts of several banks and financial sector companies around the world from 2013 to the present, in a unprecedented banking hack, said the cyber security company from Russia, Kaspersky Lab. The group, called “Carbanak” by

Google warns Microsoft and Apple: fix the vulnerability or we will disclose
Google said that its elite team consisting of hackers and programmers search security deficiencies of its software applications and other companies, Google warning that if its competitors will not eliminate vulnerabilities within 90 days, then they will make public. Google claims that software vendors must act quickly
