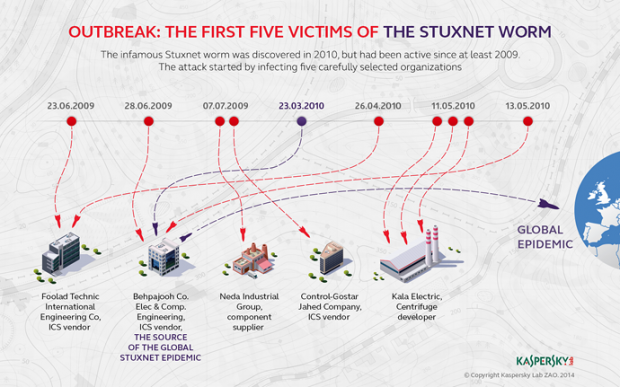
Although it has been more than four years after the discovery of one of the most sophisticated and dangerous attacks – Stuxnet worm, thought to be the first cyber weapon – there are still many uncertainties of the whole operation. The main question remains: what were the precise objectives of the operation Stuxnet? After analyzing more than 2,000 files Stuxnet collected over a period of two years, Kaspersky Lab experts can identify the first victims of computer virus.
From the beginning, the experts had no doubt that the whole attack was carefully organized. Stuxnet worm code was done professionally and dedicated; evidence indicating exploiting zero-day vulnerabilities extremely expensive. However, still not identified the typology of organizations attacked in the initial phase and how, further, malware accessed uranium enrichment centrifuges from ultra-secret locations.
Recent analyzes have revealed new information. The five organizations that were attacked initially operated in the segment Industrial Control Systems (ICS) in Iran, developing ICS systems or providing materials and components. The fifth organization that was attacked is the most interesting, because it produces including uranium enrichment centrifuges, among other industrial automation products. According to Kaspersky Lab research, this type of equipment was the main target of Stuxnet attacks.
The attackers were expecting organizations to exchange messages and data with their customers – ie uranium enrichment factories – which would have facilitated access malware in these factories. The results show that the attack was successful plan. The attackers were expecting organizations to exchange messages and data with their customers – ie uranium enrichment factories – which would have facilitated the access of malware in these factories. The results show that the attack was a success.
“Analyzing the professional activities of the first organizations to fall victim to Stuxnet gives us a better understanding of how the whole operation was planned. At the end of the day this is an example of a supply-chain attack vector, where the malware is delivered to the target organization indirectly via networks of partners that the target organization may work with,” said Alexander Gostev, chief security expert, Kaspersky Lab.
Kaspersky Lab experts have made other interesting discoveries: the Stuxnet worm was distributed not only through infected USB sticks. That was the initial theory, and it explained how the malware could access devices without internet connection. However, data gathered while analyzing the very first attack showed that the first worm’s sample (Stuxnet.a) was compiled just hours before it appeared on a PC in the first attacked organization. This time interval indicates that the attacker did not have enough time to compile the sample, to save on a USB stick and delivered it to the organization concerned. Most likely, in this case, the team behind the Stuxnet campaign has used other techniques.
The latest technical information about previously unknown aspects of the Stuxnet attack and Securelist are on a new book – Countdown to Zero Day, written by journalist Kim Zetter. The book includes new information about the Stuxnet; some of these were obtained from interviews with members of Global Research and Analysis Team at the Kaspersky Lab.
For more information, visit Kaspersky’s blog.