
Snoopy is a distributed tracking and profiling framework.
According to the British experts from Sensepost Security, the project called Snoopy demonstrates the danger of using drones without clear rules.
Sensepost created a distributed tracking and data interception framework, which performs simple tracking, real-time and historical profiling of devices and the peoples who own them. So it’s perhaps worth mentioning that Snoopy is a distributed framework compromised of various existing technologies.
How does it works?
Drones were the main stars of CES 2014 that took earlier this year in Las Vegas. New York mayor said since last year that drones will arrive in equipping police in the American metropolis.
Snoopy Drone will search for WiFi enabled devices and then using its built-in technology, it will see what networks the phones have accessed in the past and pretends to be one of those old network connections. More exactly, the Drone will use Wireless Evil Twin Attack to hack Smartphones. This attack consists in spoofing WiFi networks that the device has already accessed.
What can you do with such a drone? How dangerous is it?
This kind of attacks will allow the attacker to remote control your mobile phone or tablet. The hackers can do everything with your smartphone once they get full access to it. Researchers have successfully stolen Amazon, PayPal, and Yahoo credentials while testing it out in London. The drone hacked over 150 smartphones in one hour.
Below you can see the diagram of the Snoopy Framework’s Architecture:
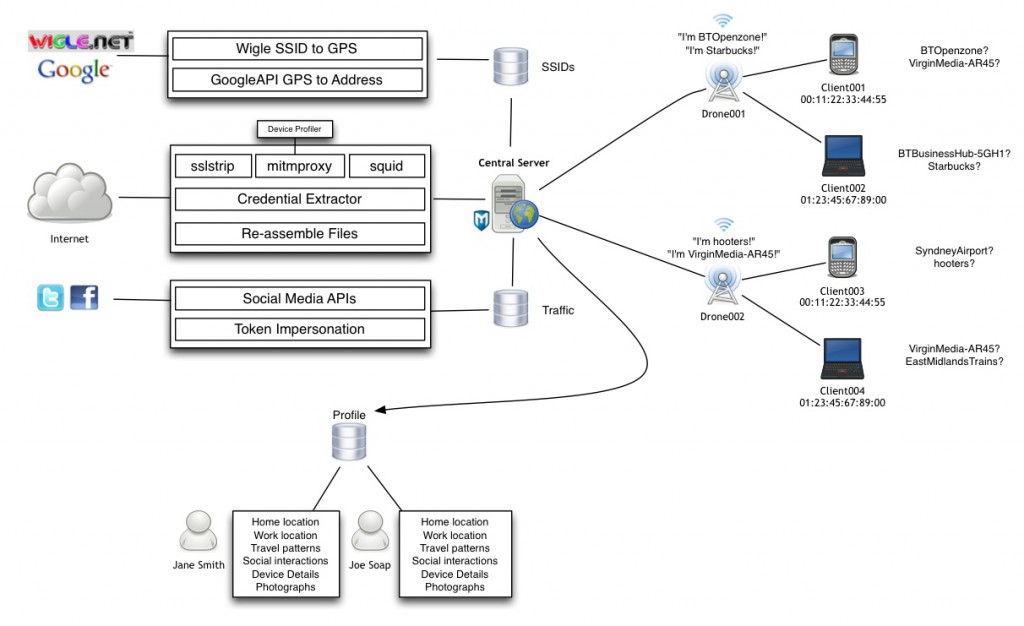
The diagram is explained on the Sensepost’s official blog.
For more techical details regarding Snoopy Framework, please see this Github Page.
You can see how Snoopy Drone works by watching the following video:

