What is a DDOS attack? And what’s the difference between DOS and DDOS attacks?
A DoS attack (Denial-of-Service) involves an attempt to disrupt operations that run a computer or network that is connected to the Internet. The most common form of DoS attack is that the operation of a computer or computer network are interrupted due to eating bandwidth computer network due to resource depletion victim or the victim system.
A DDoS attack (Distributed Denial-of Service) is a type of DoS attack, but more dangerous because it uses a network of compromised zombie computers to carry out the attack, thus not being able to identify a single source. The attacker compromises the zombie computers using special software that allows malicious attacker to use zombie computers to send messages to the victim organization creating a DoS attack.
The Story
According to Sucuri.net, any WordPress website with Pingback enabled (the pingback is enabled by default on all WordPress websites) can be used to perform DDOS attacks against other websites. XMLRPC is used for pingbacks, trackbacks, remote access via mobile devices and more features. But the XMLRPC can also be used for performing DDOS based attacks.
It all happened against a popular WordPress site that had gone down for many hours due to a DDOS attack. As the attack increased in size, their host shut them down and asked for Sucuri’s Support Team to investigate the problem. The Suciri.net team observed that over 162,000 different WordPress websites tried to attack that website. The conclusion was simple and inevitable:
WordPress Insecure Default Option = Very Large Botnet
Sucuri.net offers a simple solution for this problem, for this vulnerability. They recommend webmasters to create a wordpress plugin which adds the following filter:
add_filter( ‘xmlrpc_methods’, function( $methods ) {
unset( $methods[‘pingback.ping’] );
return $methods;
} );
Sucuri.net also created a page on their website where anybody that have a WordPress website can check to see if his website was used to perform DDOS based attack. You can find the page here.
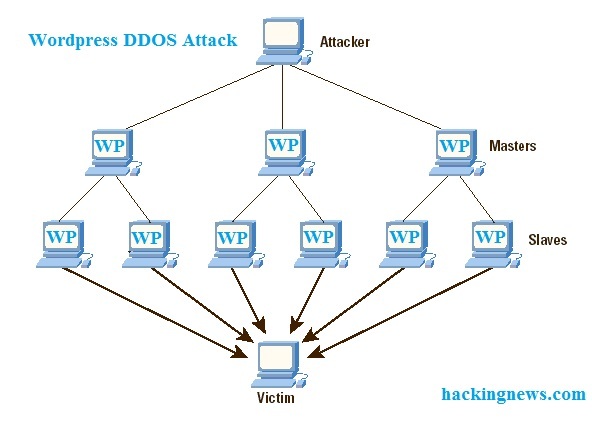
You can see in the below image how a DDOS attack works: