Magento just releasted a new security patch and they recommend us to install it immediately.
As part of our ongoing commitment to security, we have uncovered potential vulnerabilities that we are proactively addressing today with a new patch (SUPEE-6285). There are no confirmed reports of attacks related to these issues to-date, but it is important that you immediately deploy the patch in order to protect your store.
This patch addresses the following security issues:
- It prevents attackers from posing as an administrator to gain access to the last orders feed, which contains personally identifiable information that can then be used to obtain more sensitive information in follow-on attacks. Check to see if you have been compromised by reviewing your server logs for someone trying to reach the /rss/NEW location.
- It closes a number of security gaps including cross-site scripting (XSS), cross-site request forgery (CSRF), and error path disclosure vulnerabilities.
More information about these issues can be found on the Magento Security Center and in the Appendix of the Magento Enterprise Edition and Magento Community Edition user guides.
We have created patches for both Magento Enterprise and Magento Community Editions. For Magento Enterprise Edition, a patch is available for Enterprise Edition 1.9 and later releases. For Magento Community Edition, a patch is available for Community Edition 1.4.1 to 1.9.1.1 and is part of the core code of our latest release, Community Edition 1.9.2, which is now available for download.
DOWNLOADING THE SECURITY PATCH
Before implementing this new security patch (SUPEE-6285), you must first implement SUPEE-5994 (issued May 14, 2015). This will ensure that the patch works properly.
To download the patch, choose from the following options:
- Enterprise Edition Merchants: Go to My Account, select the Downloads tab, and then navigate to Magento Enterprise Edition > Support Patches. Look for the folder titled “Security Patches – July 2015.”
- Community Edition Merchants: Upgrade today to Community Edition 1.9.2 and receive the security fixes as part of the core code. Patches for earlier versions of Community Edition can also be found on the Community Edition download page (look for SUPEE-6285).
Be sure to implement and test the patch in a development environment first to confirm that it works as expected before deploying it to a production site. Information about installing patches for Magento Enterprise Edition and Magento Community Edition is available online.
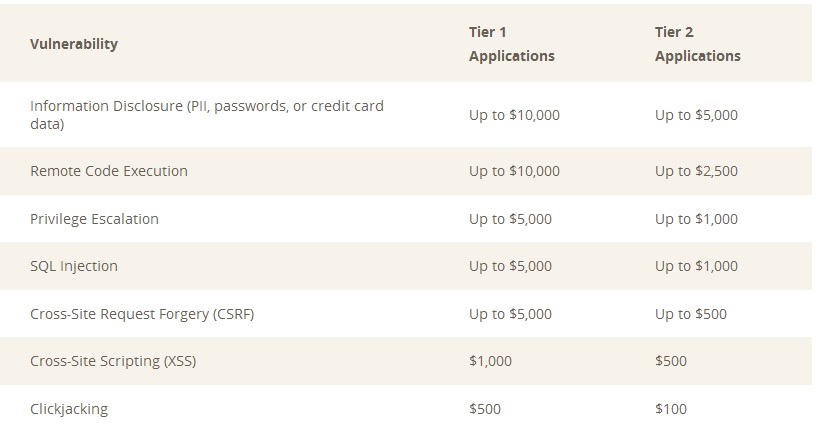
If you’re a professional pen tester, you know how to test a website in order to detect vulnerabilities, you can help Magento. Below you can find more infor regarding Magento’s bug bounty program.
Bug Bounty Payment Schedule
You may be eligible to receive a monetary reward, or “bounty,” if: (i) you are the first person to submit a site or product vulnerability; (ii) that vulnerability is determined to be a valid security issue by the security team; and (iii) you have complied with all Program Terms.
You can find more info regarding Magento’s bug bounty program here.

