vulnerability Archive

Fiverr CSRF Attack Explained ( How to avoid a phishing attack )
Fiverr.com recently suffered a Cross Site Request Forgery attack (CSRF attack). Below you’ll see a video posted by Mohamed A. Baset, a hacker that demonstrates how easy is to steal the account credentials of an anonymous user on a well known website, fiverr.com . What is CSRF?
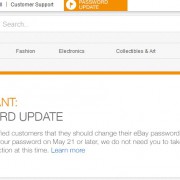
eBay hacked last week after a massive cyberattack
There are 5 days since eBay was hacked after a massive cyber attack. This attack compromised a large number of users’ personal information. Ebay is one of the world’s largest online marketplaces, they claimed 128 million active users worldwide. The group, which also owns PayPal website claimed

2014 Internet Security Threat Report
Symantec has released it’s 2014 Internet Security Threat Report. This vulnerability report presents an overview and analysis of the year in global threat activity. They reached volume 19 with this threat report. The report is based on data from the Symantec Global Intelligence Network, which Symantec’s analysts
Magento Go vulnerability allows hackers to bypass the authentication by creating administrator account
According to Securatary, this vulnerability allows for a cross store (unauthenticated, as we have not authenticated to our target store) privilege escalation attack, that will create a user on any *.gostorego.com store. There are over 200 000 active Magento Go stores. So this attack allows access to
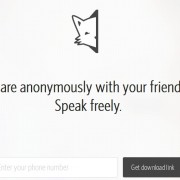
Secret.ly App Hacked, they discovered First Security Issue
The anonymous sharing app, Secret, has been recently hacked. The hack is not so serious, it doesn’t expose who said what (maybe in the future someone will expose this too). What you can be sure about, is that nothing is anonymous on the internet (excepting the Anonymous

Yahoo Mail Hacked through Third Party
Yahoo announced on their blog that hackers accessed a number of its mail accounts through a third party and that the affected accounts must reset their passwords as soon as possible. Yahoo says that their servers are still safe, but according to the company, hackers used a
