vulnerability Archive

IBM Study: Companies rethinking cyber security strategies
Approximately 60% of leaders in security believe that hackers have exceeded cybersecurity capabilities within their organization, said in a study conducted by IBM. Over 80% of security leaders believe that the challenges of external threats is increasing, while 60% agree that oraganizatiile are exceeded in this cyber war,

Pro-Russian Hacker Group CyberBerkut Claims Attack On Bundestag Websites
The German government announced on Wednesday that more of its websites, including that of the Chancellery, were victims of a major cyber attack, which was claimed by a group of pro-Russian Ukraine. The information was made public by an Executive spokesman Steffen Seibert, reports Reuters. The

The largest Bitcoin market from Europe, broken by hackers, causing millions of dollars worth of damage
Bitstamp, a major European bitcoin exchange, suspended operations after recording losses of several million dollars. Most likely, losses were recorded following a cyber attack, informs Financial Times newspaper. Bitstamp, with offices in London and Slovenia suspended the withdrawal of funds and advised clients on the danger of opening new deposits after
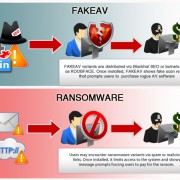
Ransomware – a malware which encrypts your data
Cyber threats have an enviable diversity and a proof of ingenuity of hackers is ransomware, a malware which encrypts your data in the “hard drive” and you can not regain access unless you pay an amount of money as a reward. Few threats act in a way so

NTP critical vulnerability, solved by OS X update
The myth which says that Apple’s operating system, OS X is more protected against hacker attacks than other operating systems was once again dismissed. A critical vulnerability that could affect Mac users proved so dangerous that led the Cupertino company to publish for the first time in

Focus on multidirectional malware and spyware on 2015
Dangerous malware such as Uroburos, spyware on Android smartphones and a growing number of cases involving malware attacks on mobile devices – 2014 was marked by cyber espionage, hacker attacks and cyber campaigns. Number of 3.5 million new strains of malware has been exceeded for the first

Pirate Bay changed their domain, again
Pirate Bay, one of the most popular for “torrent” sites, and changed the address again, for the sixth time in the last year. The Guardian reports that Pirate Bay was forced to change his domain for the sixth time in the last year, after being closed by the

Tyupkin backdoor is used in Eastern Europe for stealing money from ATM
Until now, bank’s clients risked to remain without money on their accounts after their cards were cloned with skimmers installed on ATMs. In other cases, hackers intercepted their authentication credentials using online tools and techniques. Interpol and Kaspersky announced that they discovered a network of criminals who

Shellshock bug, the error that could send Heartbleed into obscurity
A security error called “Shellshock bug” or “Bug Bash” might prove even more devastating than Heartbleed, error that impacted approximately 500,000 computers last spring, according ktvu.com. Computer security experts have analyzed Thursday the threat and installed patches on servers around the world to prevent the spread of

Tim Cook on Privacy and Apple Pay – Charlie Rose
Apple CEO Tim Cook talks about consumer privacy, data, and Apple Pay in an exclusive two-part interview. The second part airs September 15, 2014 on CHARLIE ROSE. For more, visit www.charlierose.com Below you can see some of Tim Cook’s opinions regarding the iCloud selfie scandal and also
