Breaking News Archive

Federal Communications Commission approve net neutrality rules
The Federal Communications Commission on Thursday voted to approve new rules on how the internet should be governed. New rules will prohibit internet service providers from discriminating against content producers. “Who determines how you use the internet? Who decides what content you can view and when? Should there

Android phones can be tracked just with battery power alone
We all know that a phone uses more power the further away it is from a cell tower as it tries to connect. So, an Android phone can be tracked by studying their power use over time, without using their GPS or wi-fi/data usage. Extra power is used by
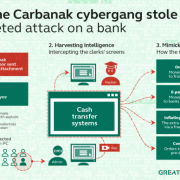
The Carbanak hacking group stole $1 billion from the accounts of several banks
A group of hackers called Carbanak stole about $1 billion from the accounts of several banks and financial sector companies around the world from 2013 to the present, in a unprecedented banking hack, said the cyber security company from Russia, Kaspersky Lab. The group, called “Carbanak” by

Google warns Microsoft and Apple: fix the vulnerability or we will disclose
Google said that its elite team consisting of hackers and programmers search security deficiencies of its software applications and other companies, Google warning that if its competitors will not eliminate vulnerabilities within 90 days, then they will make public. Google claims that software vendors must act quickly

Anthem, an insurance company, was the target of a large cyber attack
Anthem Insurance Company, the second largest in the United States, was the target of a cyber attack, hackers managed to steal personal data for many former or current clients and employees of the company, reports Reuters. Anthem announced Wednesday that hackers broke into an IT system

USBdriveby can take control of a computer in a few seconds
A few months ago was discovered a worrying vulnerability of standard USB which does not seem to be repaired, called BadUSB. Until now such information was only theoretical and no one has developed a software which can uses this security hole, but a well-known hacker Samy Kamkar has
Facebook says it was not the victim of a cyber attack, invoking technical problems
Facebook says it was not the victim of a cyber attack, invoking technical problems this morning for unavailability. Facebook invoke technical issues related to configuration changes to systems which fall off 50 minutes this morning. “The network” denies rumors which says that it was the victim of a cyber
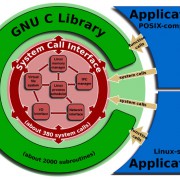
GHOST glibc vulnerability (CVE-2015-0235) affects Linux Machines
A critical vulnerability has been found in glibc, the GNU C library, that affects almost all Linux systems dating back to 2000. Attackers can use this flaw to execute code and remotely gain control of Linux machines. The Red Hat Product Security has been made aware of
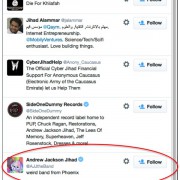
CENTCOM Twitter and YouTube accounts, hacked by a terrorist group of Islamic State
An affiliated group of terrorist network of Islamic State has conducted cyber attacks against official Twitter and YouTube accounts of US Central Command (CENTCOM), broadcasting threats against US troops, reports The Washington Post newspaper. Assigned messages of hackers have begun to appear on the CENTCOM Twitter

Pro-Russian Hacker Group CyberBerkut Claims Attack On Bundestag Websites
The German government announced on Wednesday that more of its websites, including that of the Chancellery, were victims of a major cyber attack, which was claimed by a group of pro-Russian Ukraine. The information was made public by an Executive spokesman Steffen Seibert, reports Reuters. The
